Adding a new External Service Integration
Last Updated: August 5, 2025
The steps below explain how to add a new external service integration.
Establish connectivity
From a fwdproxy instance on a given environment, try to reach the new service via whatever endpoint you have with curl. Anything over port 443 should work, but alternate ports need an ESECC request.
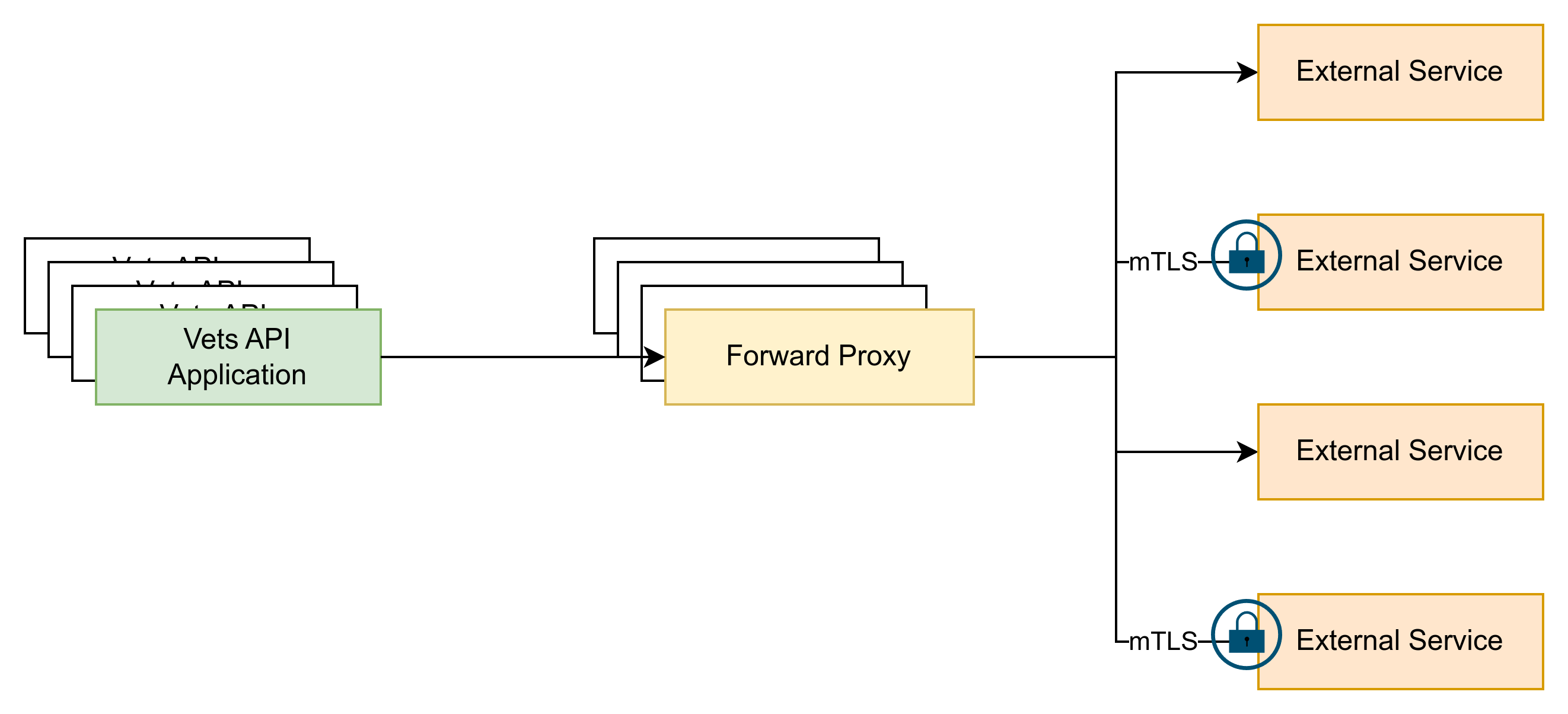
Forward Proxy
Once you have verified connectivity, add entries to the forward proxy deployments in the vsp-platform-fwdproxy repo.
SSL Keys
Many backend VA services require a client SSL certificate and key for authentication. Securely generate a private key and certificate using the instructions at: Venafi: Create and download TLS certificates. (Note: Those instructions are for Platform engineers, specifically.) Add the cert as a Jinja2 template to ansible/deployment/config/fwdproxy/, and add the private key to the AWS Parameter Store with a name like /devops/certificates/<service>.key .
NOTE: Currently, we don't impose CN restrictions on the SSL certs for new External Service Integration
Security Group / ELB config
Validate that the ports assigned for the forward proxy are listed in the listener_ports variable in terraform/environments/<env>/main.tf. The port should match what is in the Forward Proxy config above.
Rails Config
Add the required host redirects in vets-api. See these docs: https://depo-platform-documentation.scrollhelp.site/developer-docs/settings-and-parameter-store.
Healthy Traffic
The forward proxy serves several critical functions on the Platform to ensure healthy traffic. First, it performs short-circuiting (leveraging health checks) to help protect external services from getting overloaded if they become unhealthy. Second, it handles mTLS connections (see the SSL keys section above) that would otherwise need to be managed by the applications, requiring each application to redeploy any time a certificate rotates.
Centralized Service Definition
Having a central location to define all external services prevents tracking each application and its external connections (a many-to-many relationship), which prevents deploying many applications in the event of an external service definition change.
Help and feedback
Get help from the Platform Support Team in Slack.
Submit a feature idea to the Platform.
