Add certs as secrets to vets-api
Secrets for vets-api that don't fit into the settings-local-secrets ExternalSecret definition described in Vets API on EKS | Secret-Values , can be added to a different ExternalSecret section. Secrets that fall into this category are usually certificates (and the keys associated with those certs). Use this doc to help you navigate the files and sections you'll need to modify.
Steps to add certs and other uncommon secrets to vets-api
Care and attention to detail should be taken when adding secrets to vets-api–a misconfigured secret in Parameter Store or in the code will cause a vets-api pod to fail.
Prerequisites
Secret is added to AWS’s Parameter Store. Docs: Store a secret in Parameter Store
If the secret is a cert, there must be a new line at the end. One way to verify this is to click “Edit” on the parameter in the AWS Console and make sure there is an extra line at the end. It will look like this:
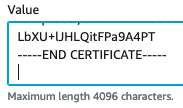
See trailing extra line
Important files
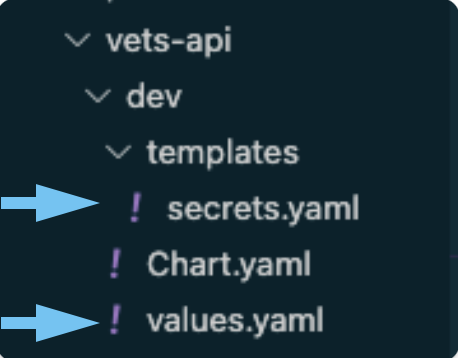
secrets and values files in vets-api dev.
You will be modifying files in the vets-api application of the vsp-infra-application-manifests repository. If you’re using the development environment, please modify dev first and then move on to the higher environments once dev is merged and tested. secrets.yaml and values.yaml are the files that need modified. See explanations below.
secrets.yaml
This file contains ExternalSecret definitions. This is where you declare how to fetch each secret. We store all of our secrets (externally) in Parameter Store (however, there are a few exceptions for items that are too large to fit in Parameter Store).
Where do you want your secrets to be mounted on the vets-api pod? The answer to this question will determine what ExternalSecret definition to add the secret to, or if a new definition is required.
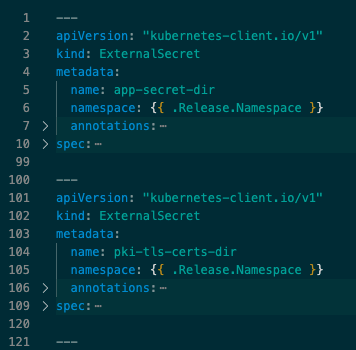
secrets.yaml Screenshot 1
Screenshot 1, for example, shows two ExternalSecret definitions: app-secret-dir and pki-tls-certs-dir. To find out where these definitions mount to, search for those names in values.yaml.
values.yaml
You will find two sections in values.yaml that mention each secret’s name, the first is the volumeMounts section and the second is the volumes section. Both of these are inside of vets-api → common. See values.yaml screenshots 1 and 2 below (sections are collapsed for clarity). Screenshot 1 shows the mountPathfor each secret definition–this is where the secrets listed in the corresponding ExternalSecret definition (from secrets.yaml) will live on the vets-api pod or container. The volumes definition will mount to the pod and the volumeMount definition will mount that specific volume to a container. If interested, see the Kubernetes documentation on https://kubernetes.io/docs/concepts/storage/volumes/.
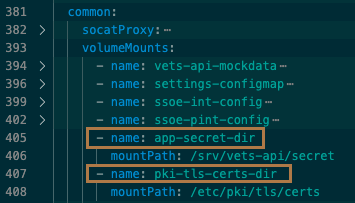
values.yaml Screenshot 1 mountPath
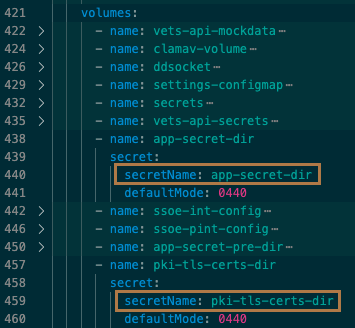
values.yaml Screenshot 2
Adding secrets
If one of the mountPaths fits your need, go ahead and an entry to the corresponding ExternalSecret definition in secrets.yaml.
If not, do the following:
Create a new
ExternalSecretdefinition insecrets.yaml, following the same conventions as the other definitions in that file. Thekeyis the Parameter Store path (tellingvets-apiwhere to look) and thenameis whatever you want the secret to be named in the container.In
values.yaml, add an entry to thevolumeMountssection. Thenamewill be whatever you named yourExternalSecretin the previous step. ThemountPathis the location in the pod you want your secret(s) mounted to.Further down in
values.yaml, add an entry to thevolumesection.nameandsecretNamewill be whatever you named yourExternalSecretin the first step.defaultModesets the permissions on the directory.
Help and feedback
Get help from the Platform Support Team in Slack.
Submit a feature idea to the Platform.
